e23996fd1f503f2d84e5058f8b221fa0c37c3f6e,sbin/db_mgmt_exploitdb.py,,,#,15
Before Change
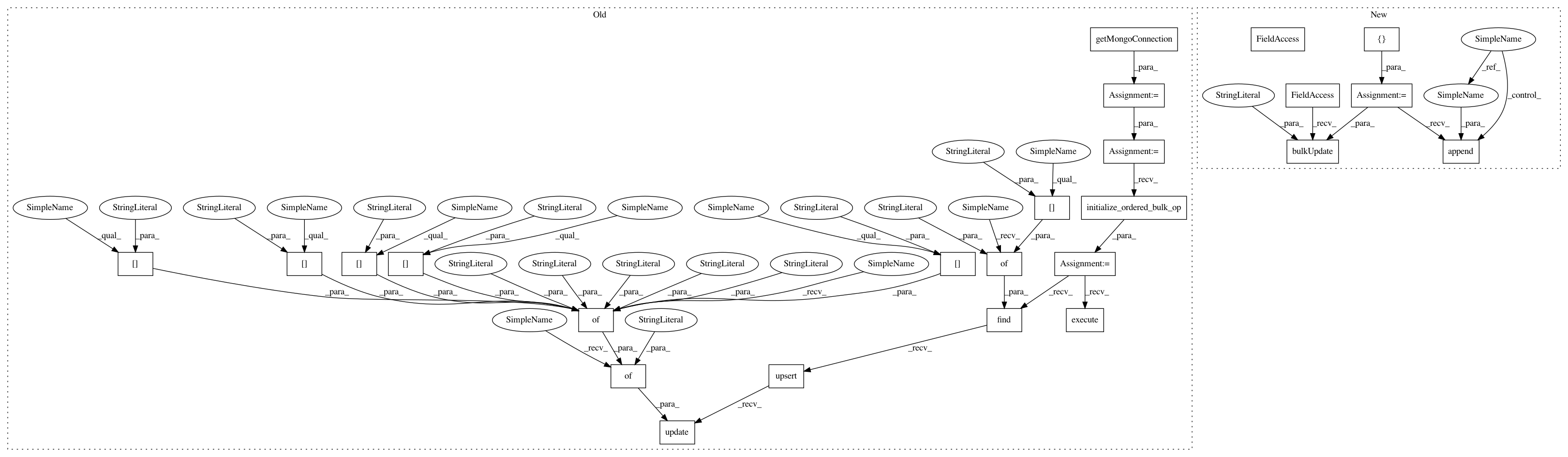
tmppath = Configuration.getTmpdir()
// connect to db
db = Configuration.getMongoConnection()
exploitdb = db.exploitdb
info = db.info
argparser = argparse.ArgumentParser(description="Populate/update the exploitdb ref database")
argparser.add_argument("-v", action="store_true", help="verbose output", default=False)
args = argparser.parse_args()
try:
f = Configuration.getFile(exploitdburl)
except:
sys.exit("Cannot open url %s. Bad URL or not connected to the internet?"%(exploitdburl))
i = dbLayer.getLastModified("exploitdb")
if i is not None:
if f.headers["last-modified"] == i:
print("Not modified")
sys.exit(0)
if not os.path.exists(tmppath):
os.mkdir(tmppath)
csvfile = tmppath+"/exploitdb.csv"
with open(csvfile, "wb") as fp:
shutil.copyfileobj(f, fp)
fp.close()
bulk = exploitdb.initialize_ordered_bulk_op()
with open(csvfile, newline="") as csvtoparse:
exploitcsv = csv.DictReader(csvtoparse, delimiter=",")
for row in exploitcsv:
if args.v:
print ("{} ({}) Imported".format(row["id"],row["description"]))
bulk.find({"id": row["id"]}).upsert().update({"$set": {"description": row["description"], "type": row["type"], "date": row["date"], "port": row["port"], "author": row["author"], "file": row["file"], "platform": row["platform"], "id": row["id"]}})
bulk.execute()
// Update last-modified
dbLayer.setColUpdate("exploitdb", f.headers["last-modified"])
After Change
shutil.copyfileobj(f, fp)
fp.close()
exploits=[]
with open(csvfile, newline="") as csvtoparse:
exploitcsv = csv.DictReader(csvtoparse, delimiter=",")
for row in exploitcsv:
exploits.append(row)
if args.v:
print ("{} ({}) Imported".format(row["id"],row["description"]))
db.bulkUpdate("exploitdb", exploits)
// Update last-modified
db.setColUpdate("exploitdb", f.headers["last-modified"])
In pattern: SUPERPATTERN
Frequency: 3
Non-data size: 24
Instances
Project Name: cve-search/cve-search
Commit Name: e23996fd1f503f2d84e5058f8b221fa0c37c3f6e
Time: 2015-10-25
Author: pieterjan.moreels@gmail.com
File Name: sbin/db_mgmt_exploitdb.py
Class Name:
Method Name:
Project Name: cve-search/cve-search
Commit Name: e23996fd1f503f2d84e5058f8b221fa0c37c3f6e
Time: 2015-10-25
Author: pieterjan.moreels@gmail.com
File Name: sbin/db_mgmt_vendorstatements.py
Class Name:
Method Name:
Project Name: cve-search/cve-search
Commit Name: e23996fd1f503f2d84e5058f8b221fa0c37c3f6e
Time: 2015-10-25
Author: pieterjan.moreels@gmail.com
File Name: sbin/db_mgmt_exploitdb.py
Class Name:
Method Name:
Project Name: cve-search/cve-search
Commit Name: 98642f1a9ed41d31cbd43a9c7407b0ca68f08823
Time: 2015-10-24
Author: pieterjan.moreels@gmail.com
File Name: sbin/db_mgmt_capec.py
Class Name:
Method Name:
